TCP listener seems to be killed or stalled
-
Hello all, I have this strange experience.
We have an NB-IOT and CAT M1 SOS button, that works 100% on a Chinese platform, but as soon as I point the button to my clients Windows Azure server or my own Linux server, it seems to kill or stall the TCP listener.
I think is has something to do with the messages being malformed, or TTL or EOL or EOF or so. But I am not an expert.
Do you have any idea how I can analyze this problem?
On my Linux, my listener is started like this:
netcat -k -l <port>and then parsed by a script.
I have a couple of cronjobs running on 3 machines that emulate the NB-IoT message. That works 100% fine, over long time.
Yet, as soon as I point the button to my Linux system, it stalls.
I don’t get it. Maybe someone here?
Thanks, Adriaan
-
@Adriaan I would recommend to do a tcpdump (but limit to the port you are using) and save it fo a file (-w option). then analyze this dump with Wireshark.
-
@Kolja-Vornholt Thanks. I have tcpdumped my ass off already.
 Anything particular that I can look for while using tcpdump?
Anything particular that I can look for while using tcpdump? -
@Adriaan Could you share a screenshot of your Wireshark Log with us?
-
Hello Kolja,
I have a tcap file, but that contains many request. I would not know what to show. I do have the idea though that the button does not always sends the [F.] flag.
I will run the following for a while:
tcpdump -i <interface> "tcp[tcpflags] & (tcp-fin) != 0" >> file.txt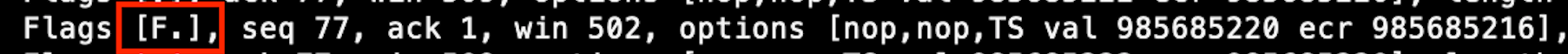
-
You think that he button does not close the TCP socket correctly (meaning without sending FIN)?
-
@Kolja-Vornholt Yes, a quick analysis hints to that, but I need more time.
Is there any way in which I can use wireshark to check pcap file for FIN messages, AND in relation to an IP number? (
Again, I am sorry, not a big expert here
Again: Thanks for your help. -
@Adriaan Can you share the pcap file with us?
-
@Kolja-Vornholt Yes. I will make a nice clean one from 1 hour or so. Ok?
-
Dear all,
Thanks to hints from @Kolja-Vornholt , I found a link that with forking works great for me: Sending the input to my parser with socat. All request will now be handled by their own fork.
Example for Linux:
socat -u TCP4-LISTEN:4445,keepalive,reuseaddr,fork STDOUT | php -f /bin/parseTCPdata4445.phpThanks to this post:
https://stackoverflow.com/questions/44886399/output-a-linux-command-to-a-url-port-or-scocket-instead-of-writing-it-to-a-file/68299500#68299500Thanks again, @Kolja-Vornholt
-
Referenced by A aliza izaton